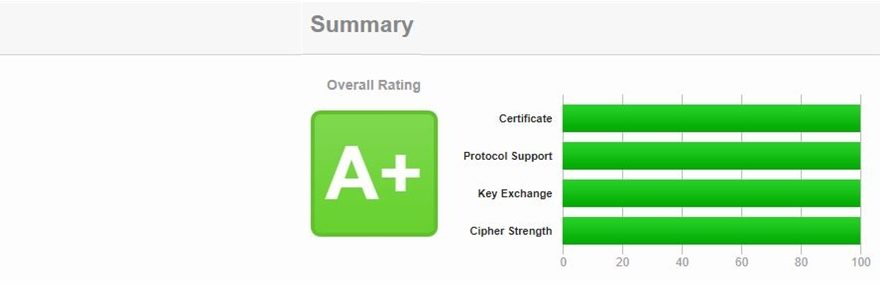
I wanted to reach A+ on the SSL Server Test and was a bit frustrated at first when it did not work out as planned. The problem lies within SSL Labs itself where one weak Cipher for TLS 1.3 still shows up active even when you explizitly denies its use in your configuration. I show you both ways having an A+ Rating without TLS 1.3 and everthing up to 100 or having an still very reasonable A+ rating with TLS 1.3 running but cipher strength down to 90. I prefer the latter.
In this setup I use a Raspberry Pi with Apache. If you use another Linux distribution or different Webserver your configuration parameters could differ from mine.
Letsencrypt cert with 4096bit
sudo certbot --apache -d your-domain.com --rsa-key-size 4096
Create dhparams
openssl dhparam -out /etc/ssl/certs/dhparams4096.pemConfigure 000-default-le-ssl.conf
ServerName your-domain.com SSLCertificateFile /etc/letsencrypt/live/your-domain.com/fullchain.pem SSLCertificateKeyFile /etc/letsencrypt/live/your-domain.com/privkey.pem Include /etc/letsencrypt/options-ssl-apache.conf ServerAdmin webmaster@localhost DocumentRoot /var/www/html ErrorLog ${APACHE_LOG_DIR}/error.log CustomLog ${APACHE_LOG_DIR}/access.log combined
Configure options-ssl-apache.conf
SSLEngine on
SSLProtocol -all +TLSv1.2 +TLSv1.3
SSLCipherSuite TLS-CHACHA20-POLY1305-SHA256:TLS-AES-256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES256-GCM-SHA384
SSLHonorCipherOrder on
SSLCompression off
SSLOptions +StrictRequire
SSLSessionTickets off
SSLUseStapling on
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLStaplingCache shmcb:/var/run/ocsp(32768)
SSLOpenSSLConfCmd ECDHParameters Automatic
#SSLOpenSSLConfCmd Curves secp521r1:secp384r1
SSLOpenSSLConfCmd Curves secp521r1
SSLOpenSSLConfCmd DHParameters "/etc/ssl/certs/dhparams4096.pem"
SSLOpenSSLConfCmd SignatureAlgorithms RSA+SHA384:ECDSA+SHA256
SSLStrictSNIVHostCheck on
# Add vhost name to log entries:
LogFormat "%h %l %u %t \"%r\" %>s %b \"%{Referer}i\" \"%{User-agent}i\"" vhost_combined
LogFormat "%v %h %l %u %t \"%r\" %>s %b" vhost_common
#Security headers
Header always set Strict-Transport-Security "max-age=63072000; includeSubdomains;"
Header always append X-Frame-Options DENY
Header edit Set-Cookie (?i)^(.*)(;\s*secure)??((\s*;)?(.*)) "$1; Secure$3$4"
Header set X-XSS-Protection "1; mode=block"
Header set X-Content-Type-Options "nosniff"
This configuration works well but let you wondering about the result in SSL Labs. You´ll only see such a result
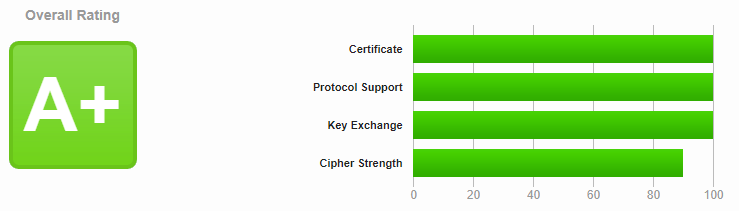
If you disable TLS 1.3 in your configuration you´ll get the full cipher strength score. Just change +TLSv1.3 into -TLSv1.3 in your options-ssl-apache.conf.
However this seems to be a bug in SSL Labs itself and is widely discussed on Git like in this posting https://github.com/ssllabs/ssllabs-scan/issues/684. Reaching a perfect score seems desirable but isn´t necessarily the best way to go in real life.